Top Posts:
Information Security
NIST 2.0: A Modern Cybersecurity Framework for All

Jonathan Cox
·July 12 2024
The National Institute of Standards and Technology’s latest Cybersecurity Framework — known in the industry as NIST 2.0 — is a powerful, flexible, comprehensive way for almost any organization to protect against the modern cyber threat landscape.
Originally adopted in 2014, as a framework for protecting critical infrastructure, NIST became the gold standard for cybersecurity risk management for any organization. NIST 2.0 is intended to reflect its wide application by making the framework far more flexibly accommodating to the needs of different organizations.
At C3, we help organizations educate their workforce on cybersecurity threats, bring their technology stacks up to a better security posture, and defend against the new era of risks. Accordingly, we take a keen interest in frameworks like NIST 2.0.
So what is it? And most importantly, what considerations should an executive make before adopting it for their organization?
What Is NIST 2.0?
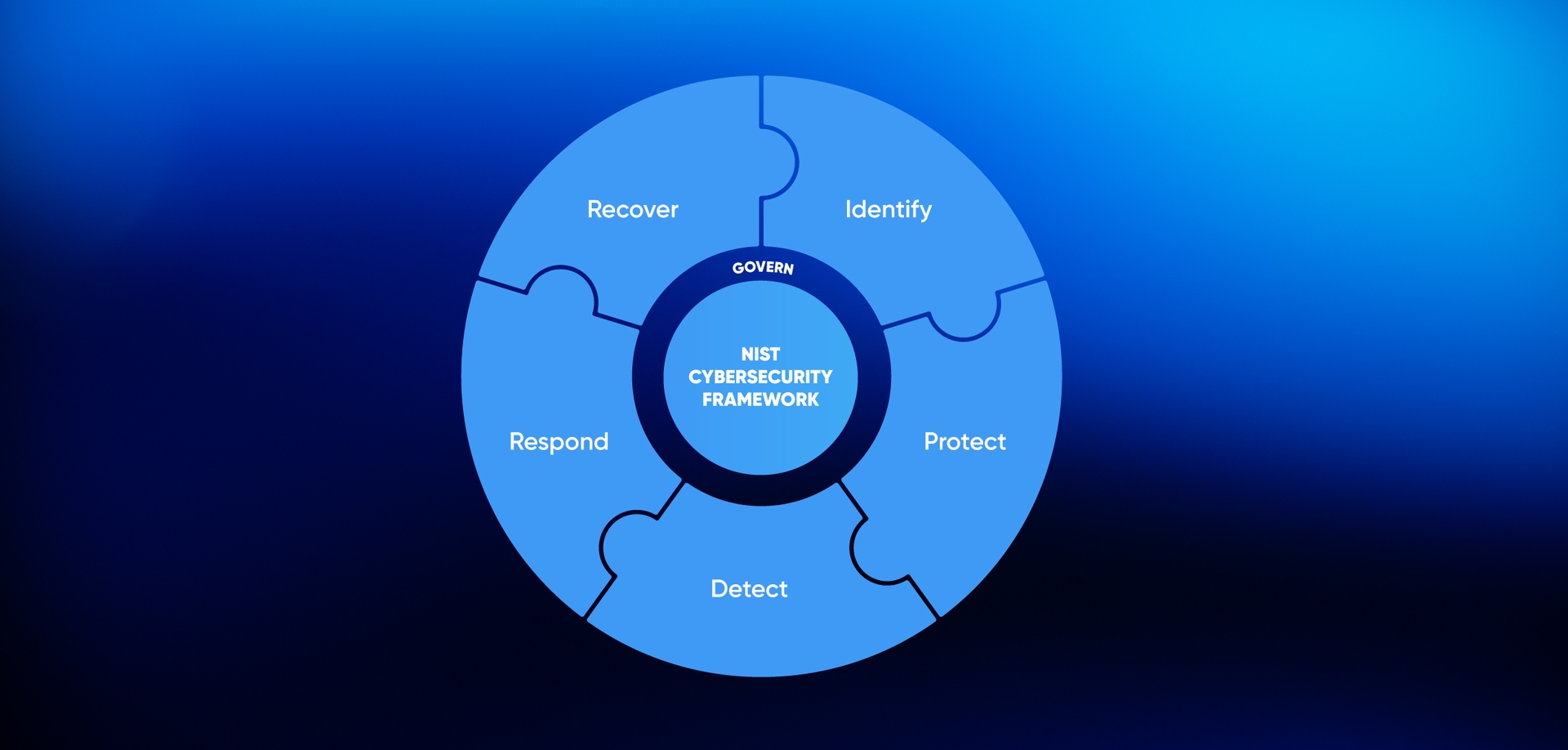
NIST 2.0 is a cybersecurity risk management framework tailored to the modern threat landscape. Intend for virtually any organization, it focuses on the most dangerous emergent threads of the last few years, particularly the proliferation of ransomware. Taken together, it is a tool to help an organization adapt its people, processes, technology, and facilities to prevent breaches from today’s threats.
NIST 2.0 can also help an executive team better manage the business continuity and disaster recovery side of a cyberattack; for instance, to better prepare financially for investment against risks year over year, and to better understand how compensating controls such as cyber liability insurance can protect you against unanticipated zero-day attacks.
As your organization invests time and resources in adopting these controls, you will improve in your organizational awareness, response, and action when a threat becomes evident. Most importantly, NIST 2.0 is about comprehensive protection — the four core quadrants of people, processes, technology, and facilities — rather than simply focusing on technology.
Getting Started With NIST 2.0
What does NIST 2.0 look like in production, and how do we get there?
We get started by conducting a NIST 800-30 assessment of your organization. This involves looking at your people, processes, technology, and facilities, and the inherent risks in each of these environments. We’ll assess a qualitative approach by looking at each one of those controls and figuring out where the organization stands.
Within IT, it’s typical to have about 20% of the general practices covered, but as we move into more robust protection assessments, gaps inevitably show up.
When you engage in a risk assessment, your top-level executive team members will move through a Q&A with an assessor, who will determine how the organization runs today. After the interview, there will be a technical control review looking at the risk exposures in your environment. It’s equivalent to a light PEN test: only looking to identify, rather than expose.
After running a series of scans both internal and external to the environment, we take our findings along with the interview materials and map out the risks we have identified against the controls. This results in a risk register that can be used to create an annual security roadmap: what you will pay attention to for the first 30-60 days, the next 60-90 days, and finally the first year.
This is your cybersecurity roadmap. It is also where a vCISO comes in handy: someone who can help manage the implementation of these recommendations, bring the organization up in its maturity over that annual cycle, and do the same thing the following year as your organization matures against the evolving threats.
Putting NIST 2.0 Into Action
Any risk framework is a journey, not a destination. Your business is constantly changing, and as these dynamics play out over an annual cycle, the risks move up and down accordingly.
A properly trained risk manager as your vCISO can navigate that path with you, help you understand and accept risks as they are introduced in the environment, and create a risk treatment plan to address those risks as they’re introduced. Eventually, you can move to an annual program that a vCISO can help you navigate to maintain that path.
Unfortunately, this isn’t something that you can simply sign off on and forget about. Effective risk assessment requires significant organizational participation. It’s usually a 3-6 week turnaround timeframe from signature to start. Ideally, we spend about 12-20 hours interviewing your organization; meanwhile, we spend anywhere from 60-100 hours completing the report, compiling the data, and identifying and categorizing risks.
Before the report is considered final, we will review a draft report with you to be sure we have everything right. Budget is the other factor: just because you should be adopting numerous security measures doesn’t mean you can adopt them all simultaneously. We will prioritize recommendations based on what you feel is appropriate for your budget, ultimately generating a final report.
Don’t Go It Alone
You should now have a good idea of how a framework like NIST 2.0 gets launched. From there, as your partner, we make sure that we are implementing all the controls that the NIST framework outlines, step by step.
My experience is that you typically need a dedicated individual who understands risk management, cybersecurity, and frameworks in order for the program to advance past the risk assessment. Trust us on this: Without someone of that caliber leading the charge, your cybersecurity roadmap has a very low likelihood of being managed. After all, running your business is a full-time job, and simple awareness doesn’t mean you have the time or skillset to implement risk measures. If it were that easy, there wouldn’t be 7+ million cybersecurity job vacancies waiting to be filled right now.
This is also the reason the vCISO model works so well. We strongly believe that being under contract with a risk specialist who is committed to implementing the model is the best defense for most mid-sized organizations, and the best way to get the NIST 2.0 framework operational.
Watch The Webinar
Ready to learn more?
In this ChannelVision webinar, I explain how leveraging the NIST CSF 2.0 framework can streamline compliance and improve overall cybersecurity posture.

About The Author
Jonathan Cox is the Vice President of Information Security at C3 Complete. As a seasoned technology infrastructure executive, Mr. Cox has made significant contributions in his roles as a COO, Vice President of Information Security, Performance Management Coordinator, Cybersecurity Risk Management Expert, and Software as a Service (SaaS) Delivery Architect.



